Avira VPN (2.15.2.28160) Elevation of Privilege through Insecure Update location
Product Version: Avira Phantom VPN
Downloaded from: https://package.avira.com/package/oeavira/win/int/avira_en_vpn__ws.exe
Operating System tested on: Windows 10 1709 (x64)
Vulnerability: Avira VPN Elevation of Privilege
Brief Description: The Avira Phantom VPN Service performs a handful of checks when it checks for an update (this happens when the service starts, so on boot or via manual start/stopping). When updating, the VPN service downloads the update to “C:WindowsTemp” as AviraVPNInstaller.exe (which any user can write to). It then checks if the file is signed, and if the version is less than the installed product version. If these requirements are met, the service will run the update binary as SYSTEM. It is possible to overwrite “AviraVPNInstaller.exe” with a signed, valid Avira executable (with a version greater than the installed version) that looks for various DLLs in the current directory. Due to the search order, it is possible to plant a DLL in “C:WindowsTemp” and elevate to NT AUTHORITYSYSTEM.
Vulnerability Explanation
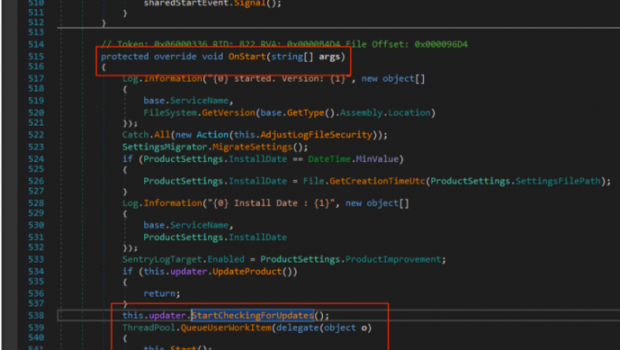
When the Avira VPN service (Avira.VPNService.exe, version 2.15.2.28160) starts, it checks to see if there is an update available:
After some poking, it was determined that the VPN service updates from “C:WindowsTemp”
As you may know already, any authenticated user can write (but not read) to C:WindowsTemp. Once the update is there (as C:WindowsTempAviraVPNInstaller.exe), the VPN service checks the “FileVersion” property of the executable in order to determine if the “update” is already installed on the system:
If the version of the file shows it hasn’t been installed, the service will check the file to make sure it is valid and signed by Avira:
If the file is indeed valid and signed by Avira, the VPN service will start the “update” package. Since all of this happens in a place a low privilege user can write to, it is possible to hijack the update package and perform DLL sideloading.
In order to hijack “AviraVPNInstaller.exe”, three of the following conditions have to be met:
- “AviraVPNInstaller.exe” has to be signed by Avira
- The signature on “AviraVPNInstaller.exe” has to be valid (any modification of that file would invalidate the signature
- The version number of “AviraVPNInstaller.exe” proves the update hasn’t been installed on the system.
This means we need to abuse an Avira signed file that has a version greater than what is deployed.
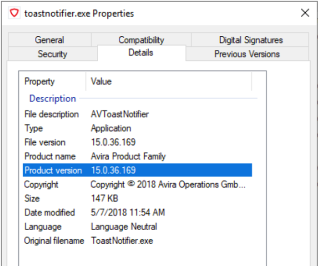
After some hunting, “ToastNotifier.exe” fit the bill as it satisfies all three requirements:
(If you are curious of where ToastNotifier.exe came from, it is from the Avira Antivirus product suite that was abused in a similar manner in a bug reported on the Antivirus platform).
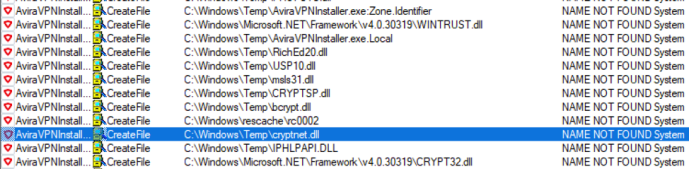
To exploit this, all we need to do is copy “ToastNotifier.exe” to “C:WindowsTempAviraVPNInstaller.exe”. Since the requirements are met, the VPN service will run it as SYSTEM when the service restarts. This can be accomplished via a reboot, or by running powershell as an Administrator and then doing “Get-Service AviraPhantomVPN | Stop-Service” followed by “Get-Service AviraPhantomVPN | Start-Service”. Once executed, “ToastNotifier.exe” (which is now C:WindowsTempAviraVPNInstaller.exe) will try to load a handful of DLLs out of C:Windowstemp:
To elevate our privileges to SYSTEM, all we need to do is provide one of those DLLs. In this case, we will hijack “cryptnet.dll”. This will result in the VPN service starting our “AviraVPNInstaller.exe” binary as SYSTEM, which will then load “cryptnet.dll” as SYSTEM, which is our malicious code. This results in elevation from a low privileged user to SYSTEM:
Disclosure Timeline:
- Submitted to Avira on September 28, 2018
- October 1, 2018: Issue reproduced by Avira
- December 13, 2018: Issue fixed by Avira











Gloss