Avira VPN 2.15.2.28160 Elevation of Privilege
Product Version: Avira Phantom VPN version 2.15.2.28160
Downloaded from: https://package.avira.com/package/oeavira/win/int/avira_en_vpn__ws.exe
Operating System tested on: Windows 10 1803 (x64)
Vulnerability: Avira VPN Elevation of Privilege
Brief Description: The Avira Phantom VPN service changes the DACL on “C:ProgramDataAviraVPNVpnSharedSettings.backup” and “C:ProgramDataAviraVPNVpnSharedSettings.config” when a configuration change is made in the VPN settings menu. By setting a hardlink on “C:ProgramDataAviraVPNVpnSharedSettings.backup”, it is possible to overwrite the DACL on an arbitrary file, leading to elevation from a low privileged user to SYSTEM.
Vulnerability Explanation
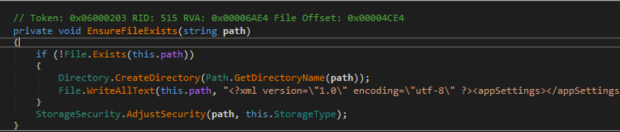
When making a configuration change via the VPN GUI, the VPN service (Avira.VPNService.exe) calls the function “AdjustSecurity()” that resides in “Avira.VPN.Core.dll” to change the DACL to allow any authenticated user to write to “C:ProgramDataAviraVPNVpnSharedSettings.backup” or “C:ProgramDataAviraVPNVpnSharedSettings.config”. When a configuration change is made (which can be done as a low privileged user), the service makes sure the “Shared” VPN profile setting file (C:ProgramDataAviraVPNVpnSharedSettings.backup and C:ProgramDataAviraVPNVpnSharedSettings.config) exist by calling “EnsureFileExists()”:
If the configuration file doesn’t exist, the service will create it and continue. If it does, it simply continues to the “StorageSecurity.AdjustSecurity()” function. In the case of the shared vs private configuration profiles, the “StorageType” being passed is either “AllUserAccess” or “Secure”. The “private” VPN profile is assigned the “Secure” storage type while the shared profile is assigned “AllUserAccess”.
When the “AdjustSecurity()” function is called (passing the storage type of the configuration file), it adjusts the DACL on the file itself appropriately. This is where the bug lies. For the “shared” profile (with the StorageType of “AlluserAccess”), the VPN service calls “AdjustSecurity()” and grants the everyone full control over the file:
This is dangerous because the “SetAccessControll()” call changes the DACL on a file in which a low privileged user can control. So, how do we exploit this?
First, an attacker needs to create a hardlink on “C:ProgramDataAviraVPNVpnSharedSettings.backup” and point it at a file. In this case, we will point it at “C:Program Files (x86)AviraVPNOpenVPNphantomvpn.exe”. Doing so will overwrite the DACL on “C:Program Files (x86)AviraVPNOpenVPNphantomvpn.exe”.
After doing so, open the VPN and click the “Settings” tab:
After doing so, uncheck the “Send Diagnostic Data” box. This will trigger a config change and kick the code-path off:
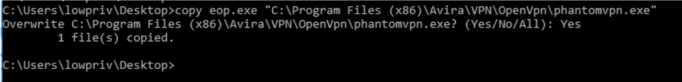
At this point, the DACL on “C:Program Files (x86)AviraVPNOpenVPNphantomvpn.exe” has been overwritten to allow any user to write to it. The attacker now just needs to copy a malicious binary to replace it:
Once done, execution of the malicious binary can be accomplished by simply trying to connect to the VPN. This can be done by clicking “Secure my Connection” in the VPN GUI:
After clicking “Secure my connection”, you should see a few cmd.exe processes running as SYSTEM:
Disclosure Timeline:
- Reported to Avira on September 28, 2018
- October 1, 2018: Avira acknowledged the report
- October 4, 2018: Avira was able to reproduce
- December 13, 2018: Issue resolved














Gloss