Another Magento Remote Code Execution Vulnerability
The security expert Ebrahim Hegazy has published an interesting post detailing his discovery of a new Magento Remote Code Execution Vulnerability.
The popular hacker Ebrahim Hegazy (Aka Zigoo) has discovered a Remote Code Execution Vulnerability that affects the widely adopted application Magento.
The experts was analyzing the Magento website whe he discovered the sub-domain https://lavender.dev.magento.com/ supposedly used as a development server. He decided to analyze it and discovered the Magento installation folder https://lavender.dev.magento.com/GitHub/setup/
[adsense size='1']
Then the hackers tried to install the applications from the folder:
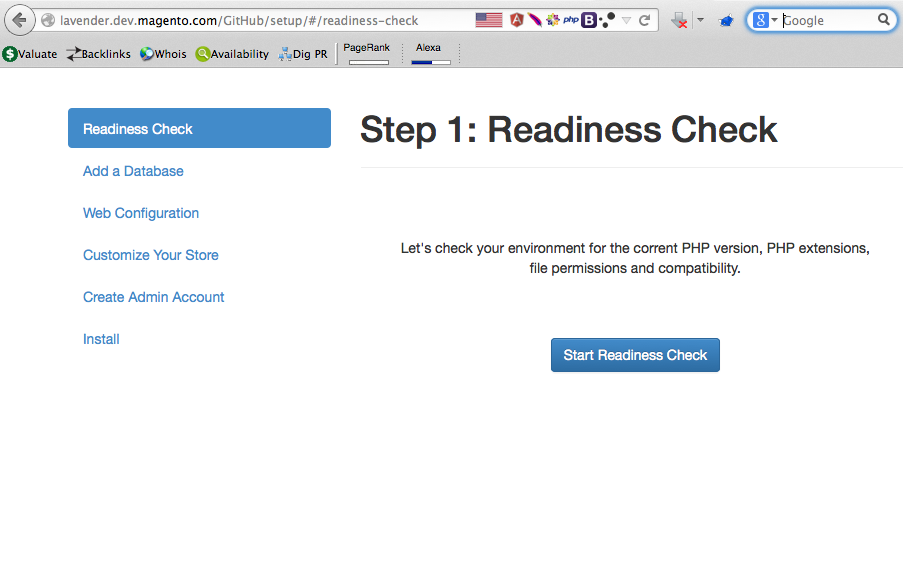
He noticed that the installation wizard allows users to name the admin login page without restriction, for example, it is possible to name it “admin” or “cpanel”.
[adsense size='1']
Ebrahim used the URL https://lavender.dev.magento.com/GitHub/setup/#/add-database to configure a database for the Magento but he provided bogus database credentials in order to force an error as reported in the following image:
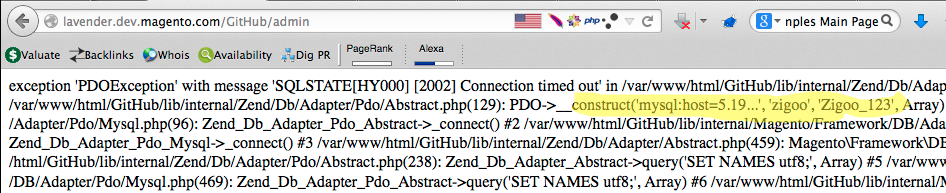
The experts noticed that the message associated to the exception includes the credentials he has submitted.
To recap, the attack scenario to trigger the RCE is:
- I will provide a bogus ip so the database will through an error, and that error will be reflected in the “Admin” page i created.
- Because i can rename the admin panel to whatever, so i will rename it to “zigoo.php”, now the error will be inserted into “zigoo.php” page.
- Since the data i provided in the db username and password inputs are reflected in the “.php” page, i will inject a PHP code inside the username & password fields.
Then the expert added php code “<?phpinfo();?>” in the username & password field, and renamed the admin panel to be “zigoo.php” and add bogus ip in the “Database Server Host” field as below:
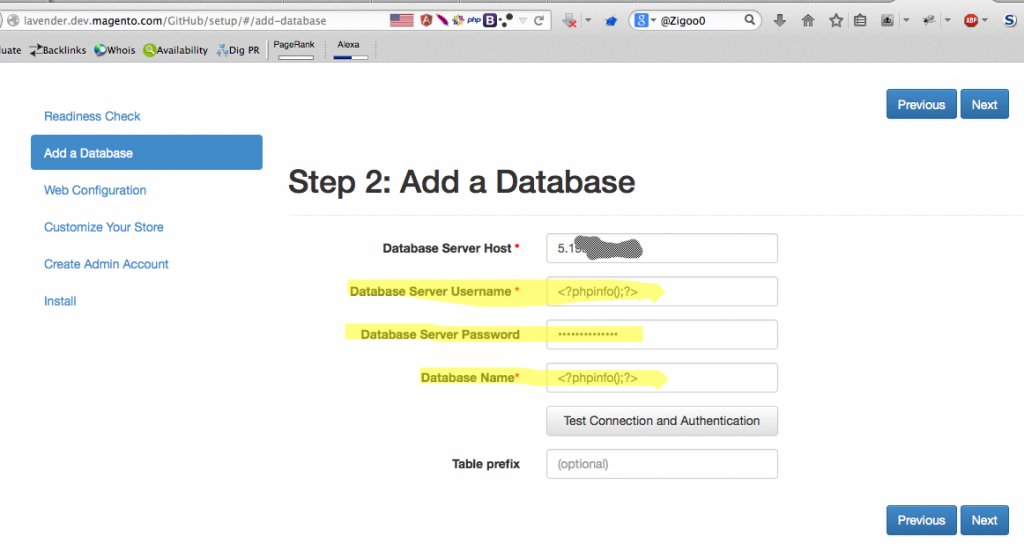
“And Pingo! RCE triggered and the php code “<?phpinfo();?>” worked like a charm!”
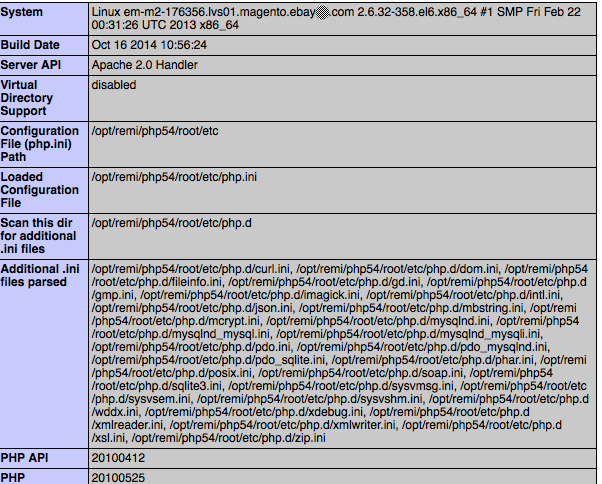
How to mitigate the vulnerability?
To fix this flaw users need to remove the installation files/directory or at least rename it.
[adsense size='1']
If you are interested about the vulnerability timeline give a look to the post published by Ebrahim Hegazy.








Gloss