Android Malware Abuses App Permissions to Hijack Phones | News & Opinion
https://www.ispeech.org/text.to.speech
Android users beware: Hackers are taking advantage of a flaw in the OS that can trick you into giving up access to your phone.
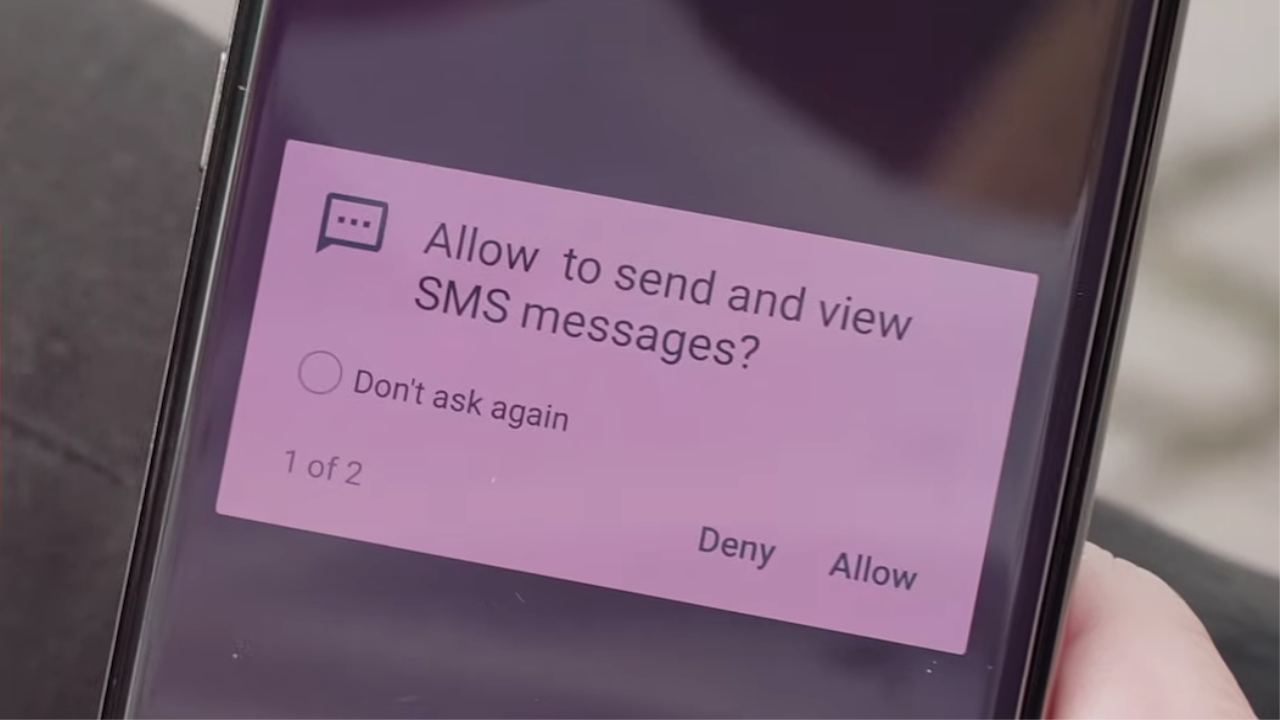
On Monday, security researchers in Norway disclosed "Strandhogg," a vulnerability that can exploit the permission pop-up windows on Android. Ironically, the permission pop-ups are meant to be a safety feature; if an app wants access to your phone's SMS messages, camera or contacts, it first needs to get your approval.
The feature is a handy tool to prevent apps from automatically accessing any sensitive data or functions on your phone. Unfortunately, the same safeguard has a flaw. The security firm Promon has uncovered hackers using malicious Android software to overlay fake permission pop-ups on top of legitimate ones.
Users who click on the pop-ups may assume, "Oh, I'm letting Instagram or Twitter access my phone's storage. Sure, that's fine." But in reality, they're opening the door for the hacker's malicious app to dive right in.
"An attacker can ask for access to any permission, including SMS, photos, microphone, and GPS, allowing them to read messages, view photos, eavesdrop, and track the victim's movements," Promon said in the company's report. "The attack can be designed to request permissions which would be natural for different targeted apps to request, in turn lowering suspicion from victims."
The same flaw can hijack the permission pop-up for any Android app. In addition, it can also overlay look-alike login windows on top of a social media or banking app to dupe you into handing over your passwords.
The vulnerability exists thanks to multitasking system in Android called "taskAffinity," which can inadvertently let a malicious app assume the identity of another app on board the OS, Promon said. The security firm uncovered the threat after customers of several banks in the Czech Republic reported their money mysteriously disappearing from their accounts. A company partner then supplied Promon with a live sample of the Android malware that exploited the flaw.
Android #StrandHogg vulnerability
Vulnerability allows malicious app to masquerade as any other app on the device.
So, if you launch Facebook, malware is executed.
See video demo how it works.https://t.co/19r1vPjQPY @Promon_Shield pic.twitter.com/F4Jie8bnQ1
— Lukas Stefanko (@LukasStefanko) December 2, 2019
To deliver the attack, the hackers have been secretly using "dropper apps" and "hostile downloaders" over the Google Play Store. These apps can be harmless at first, but will secretly download the Strandhogg-based malware to the vicitm's phone at a later time.
In response to the threat, Google said it's removed the harmful apps from the Play Store. The company's built-in malware protection software for Android, Google Play Protect, has also been updated to block apps from using the Strandhogg attack. "Additionally, we're continuing to investigate in order to improve Google Play Protect's ability to protect users against similar issues," a company spokesperson added.
Nevertheless, Promon claims Google hasn't patched the Android OS itself from the Strandhogg attack. In total, 36 malicious apps —some sourced back to 2017— have been found using the vulnerability, according to Promon's partner on the investigation, Lookout. Oddly, none of the companies involved named which apps were affected, making it unclear the scale of the threat.
So how can you protect yourself? The attack comes from malicious apps. So it's best to avoid third-party app stores outside of Google Play and to refrain from downloading apps from little-known developers.
Promon also advises users to be on guard against apps requesting permissions they don't need. For example, a calculator app asking for GPS permission. If you suspect something shady is occuring, uninstall the app immediately.







Gloss