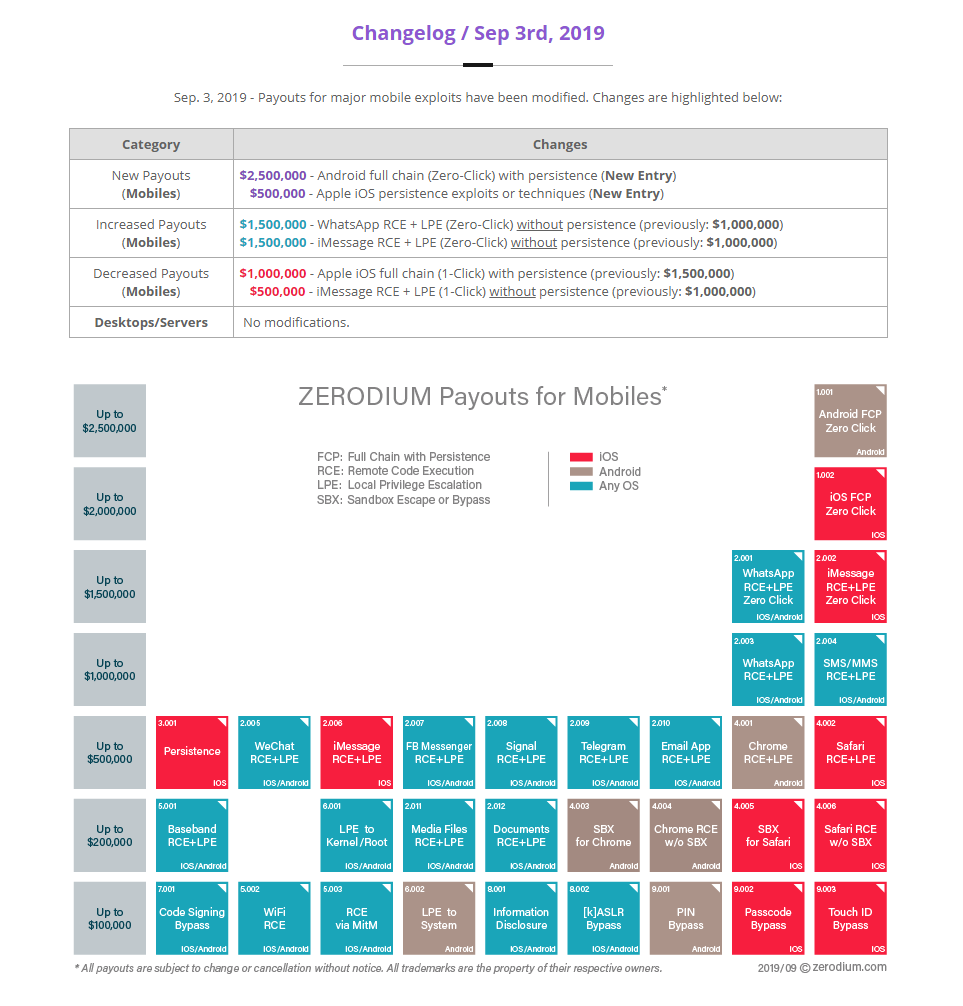
Controversial exploit trader Zerodium now pays more for unpatched vulnerabilities affecting Google's Android operating system than Apple's iOS equivalent, for the first time.
An Android zero-click full-chain exploit that persists on compromised mobile devices can earn sellers up to US$2.5 million.
In comparison, Zerodium pays up to US$2 million for an equivalent iOS exploit chain.
Zerodium also dropped its rates for a single-click full-chain exploit for iOS that persists from US$1.5 million to US$1 million.
Single-click Apple iMessage remote code execution and local privilege escalation bugs without persistence only bring in half of what they used to, at US$500,000.
However, a zero-click, non-persistent remote code execution and local privilege escalation vulnerabilty in iMessage is now worth US$1.5m - up from US$1m - ditto the equivalent exploit for WhatsApp, Zerodium said.
Zerodium did not say why it has changed the pricing for iOS and Android vulnerabilties so dramatically. Its founder Chaouki Bekrar tweeted a screenshot of a US media story claiming that iOS exploits are flooding the market currently.
The price changes come in the wake of Google's Project Zero security team publishing details of 14-exploit chain of zero-day vulnerabilties loaded into hacked websites, and which were used to fully compromise Apple iOS devices.
While Project Zero did not identify the websites in question, United States media quoted unnamed sources saying that the attacks were targeting Uyghurs, a minority group being harshly suppressed by Chinese authorities.
Zerodium also trades in desktop and server OS and application vulnerabilties, and says its customers "are mainly government organisations in need of specific and tailored cybersecurity capabilties, and/or protective solutions to defend against zero-day attacks."
The exploit reseller says its products and services are highly restricted and only available to a limited number of organisations.
Bekrar ran another exploit trading company, the now defunct VUPEN, that counted the United States National Security Agency among its customers.







Gloss