Access Controls Part 2: Computer Security Lectures 2014/15 S2
iSpeech.org
This video is part of the computer/information/cyber security and ethical hacking lecture series; by Z. Cliffe Schreuders at Leeds Beckett University. Laboratory work sheets, slides, and other open educational resources are available at http://z.cliffe.schreuders.org.
The slides themselves are creative commons licensed CC-BY-SA, and images used are licensed as individually attributed.
Topics covered in this lecture include:
Filesystems
Metadata: information about data
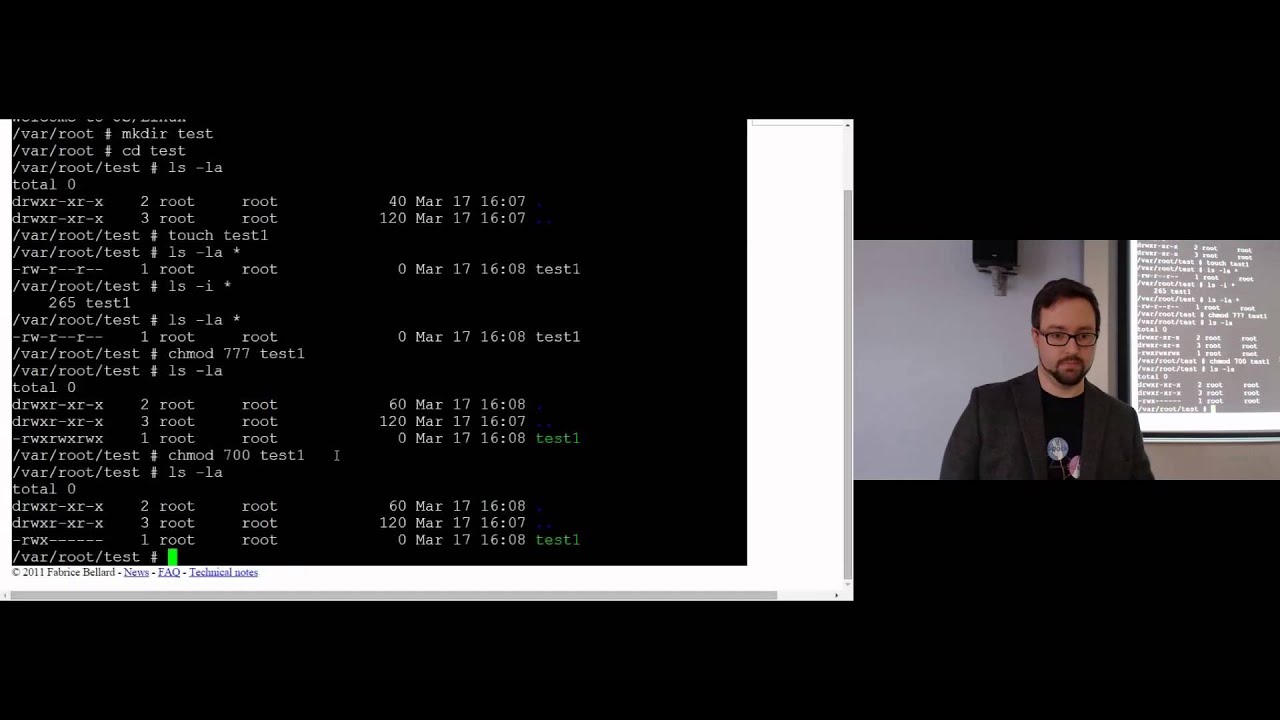
Unix Filesystems
Every file has an inode
Type, size, last modified, etc#
The files owner (UID) and group (GID)
File permission bits
Unix Directories
Everything on Unix is a file
A directory is a special type of file
It contains a list of names that it contains
And their inode numbers
Provides a mapping between names and inodes
Unix uses an abbreviated form of access control list
For example, Joe r, Frank wr, and Eve r
The first few bytes describe what type of executable it is
You can your own executable file by starting a text file as #!/bin/bash, then grant execute permission
Changing permissions on a Linux system
chmod command
umask
user file-creation mode mask
It strips permissions from the default 666 for files or 777 for new executables (logical NOT)
Unix identity: SUID
Sometimes a user needs to be able to do things that require permissions that they should not always have
The ping command needs raw network access... Again not something that every user can do
The Unix solution is set UID (SUID)
Processes can be given permission to run as another user
Every process actually has multiple identities, including:
The real UID (RUID): the user who is running the command
The effective UID (EUID): the way the process is treated
ps -eo ruser,euser,comm
The “s” means use the file UID as the effective UID
Linux Extended ACLs
Modern Linux systems (and some other Unix-based systems) now have more complete (and complicated) ACL support
Linux Extended ACLs
Set File ACLs
Detect File ACLS
Get File ACLs
2015-06-13 14:47:34
source







Gloss