Browsing the "Gadget" Category

Published on May 13th, 2024 | by admin
iSpeech May 13, 2024NewsroomSoftware Security / Malware Cybersecurity researchers have identified a malicious Python package that purports to be an offshoot of the popular requests library and has been found concealing a Golang-version of the Sliver... Read More →

Published on May 11th, 2024 | by admin
french tts The financially motivated threat actor known as FIN7 has been observed leveraging malicious Google ads spoofing legitimate brands as a means to deliver MSIX installers that culminate in the deployment of NetSupport RAT. "The... Read More →

Published on May 10th, 2024 | by admin
natural text to speech May 10, 2024NewsroomMalware / Cyber Espionage The North Korean threat actor tracked as Kimsuky has been observed deploying a previously undocumented Golang-based malware dubbed Durian as part of highly-targeted cyber attacks aimed... Read More →

Published on May 10th, 2024 | by admin
iSpeech May 10, 2024The Hacker NewsArtificial Intelligence / Threat Hunting Artificial intelligence (AI) is transforming cybersecurity, and those leading the charge are using it to outsmart increasingly advanced cyber threats. Join us for an exciting webinar,... Read More →

Published on May 10th, 2024 | by admin
Powered by iSpeech May 10, 2024NewsroomBrowser Security / Vulnerability Google on Thursday released security updates to address a zero-day flaw in Chrome that it said has been actively exploited in the wild. Tracked as CVE-2024-4671, the... Read More →

Published on May 10th, 2024 | by admin
TTS Demo May 10, 2024NewsroomBrowser Security / Vulnerability Google on Thursday released security updates to address a zero-day flaw in Chrome that it said has been actively exploited in the wild. Tracked as CVE-2024-4671, the high-severity... Read More →

Published on May 10th, 2024 | by admin
TTS Demo May 10, 2024NewsroomVulnerability / Cloud Security Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target cloud-hosted large language model (LLM) services with the goal of selling access to other... Read More →

Published on May 9th, 2024 | by admin
iSpeech May 09, 2024NewsroomEncryption / Data Privacy Researchers have detailed a Virtual Private Network (VPN) bypass technique dubbed TunnelVision that allows threat actors to snoop on victim's network traffic by just being on the same local... Read More →

Published on May 9th, 2024 | by admin
text to speech May 09, 2024NewsroomMobile Security / Cyber Attack Polish government institutions have been targeted as part of a large-scale malware campaign orchestrated by a Russia-linked nation-state actor called APT28. "The campaign sent emails with... Read More →

Published on May 9th, 2024 | by admin
iSpeech.org May 09, 2024The Hacker NewsvCISO / Regulatory Compliance Cybersecurity and compliance guidance are in high demand among SMEs. However, many of them cannot afford to hire a full-time CISO. A vCISO can answer this need... Read More →

Published on May 9th, 2024 | by admin
iSpeech.org May 09, 2024NewsroomFirewall / Network Security Two security vulnerabilities have been discovered in F5 Next Central Manager that could be exploited by a threat actor to seize control of the devices and create hidden rogue... Read More →
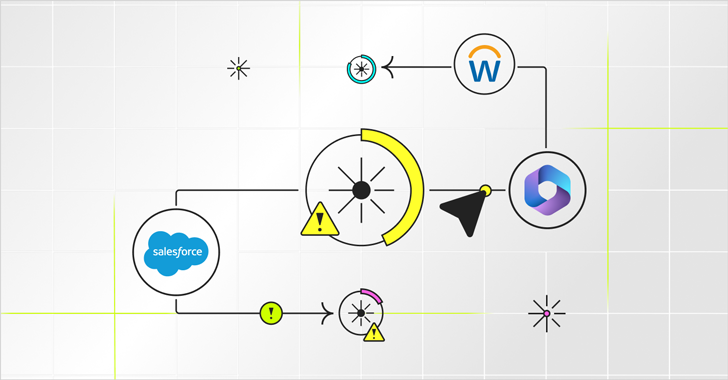
Published on May 8th, 2024 | by admin
iSpeech.org Permissions in SaaS platforms like Salesforce, Workday, and Microsoft 365 are remarkably precise. They spell out exactly which users have access to which data sets. The terminology differs between apps, but each user's base permission... Read More →

Published on May 8th, 2024 | by admin
https://www.ispeech.org Artificial intelligence is forcing many companies to evolve and rethink how to govern and analyze data, according to survey results released Monday by Gartner. Based on a survey of 479 chief data and analytics officers,... Read More →

Published on May 8th, 2024 | by admin
https://www.ispeech.org May 08, 2024NewsroomEncryption / Information Stealer A newer version of a malware loader called Hijack Loader has been observed incorporating an updated set of anti-analysis techniques to fly under the radar. "These enhancements aim to... Read More →





















Gloss