5 Key Areas to Consider When Building an Effective Vulnerability Management Program
iSpeech.org
The purpose of an organization’s Vulnerability Assessment program is to establish controls and processes that will help the organization identify its vulnerabilities within the firm’s technology infrastructure and information system components. This is essential because these vulnerabilites can potentially be exploited by attackers who seek to gain unauthorized access to the organization's systems, disrupt its business operations, and steal or leak sensitive data.
The purpose of an organization's Patch Management program and policy is to identify controls and processes that will provide the organization with the appropriate protection against the vulnerabilities and threats identified by the vulnerability assessment program. These vulnerabilities and threats could adversely affect the security of the organization’s information system or data entrusted on the information system.
In this live webinar, join Cyber Security Expert, Derek A. Smith, who will examine ways to build an effective vulnerability and patch management program. He will show attendees how to effectively implement controls that could create a consistently configured environment that is secure against known vulnerabilities. Derek will also examine 5 key areas:
1. The threat monitoring process; the ongoing process of gathering information about new and emerging threats to an organization's IT assets.
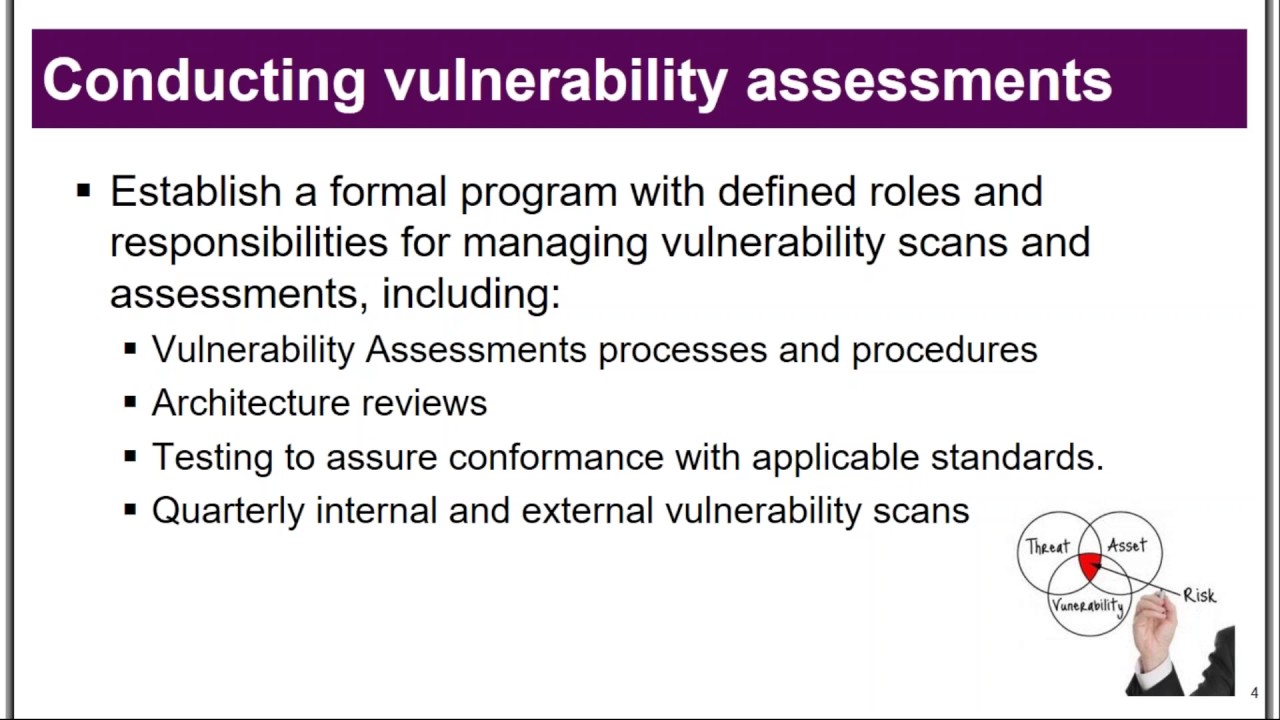
2. Conducting vulnerability assessments; identify and analyze vulnerabilities associated with technology assets.
3. Configuration management; the practice of standardizing the configuration of similar technology assets based on documented configurations in accordance with applicable policies.
4. How to perform vulnerability remediation management; to evaluate identified vulnerabilities, assign risk based on likelihood and impact, plan an appropriate response, track the response through completion, and periodically verifying completion.
5. Examine the vulnerability and patch management detailed process phases; including components of patch management and their requirements.
2017-04-20 18:36:30
source







Gloss