2016 – James Kettle – Hunting Asynchronous Vulnerabilities
iSpeech.org
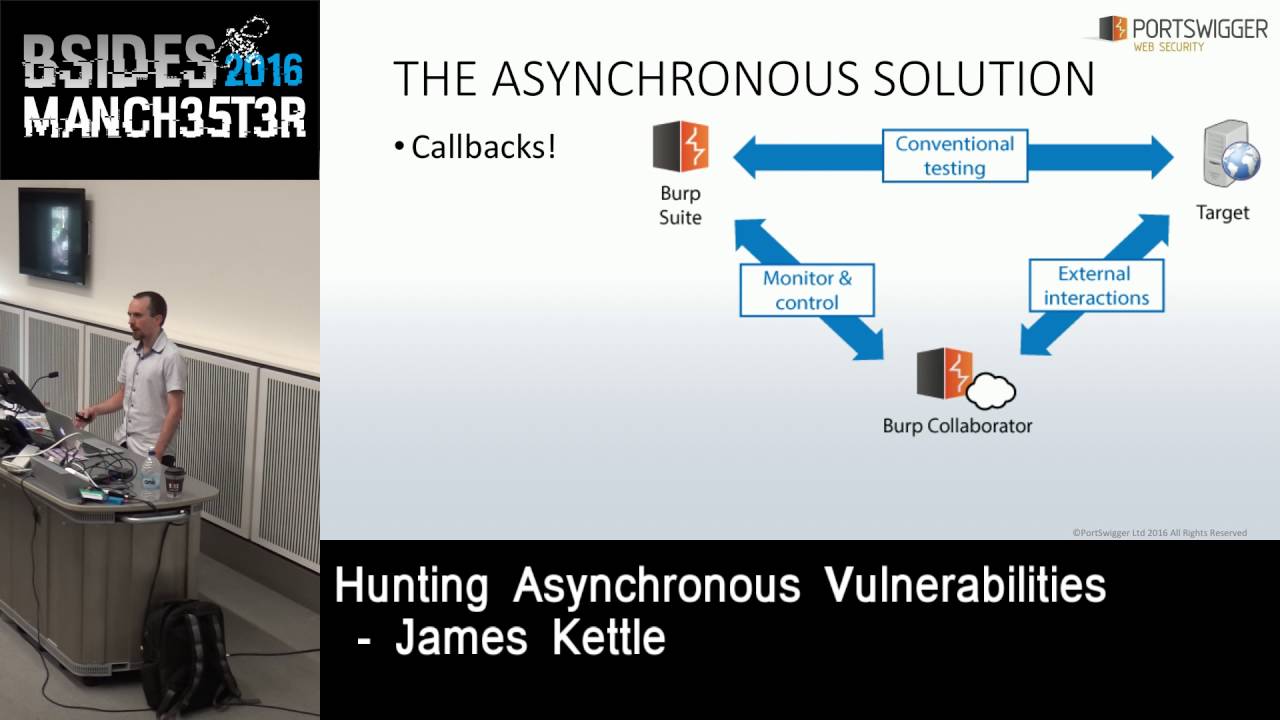
In blackbox tests vulnerabilities can lurk out of sight in backend functions and background threads. Issues with no visible symptoms like blind second order SQL injection and shell command injection via nightly cronjobs or asynchronous logging functions can easily survive repeated pentests and arrive in production unfixed.
The only way to reliably hunt these down is using exploit-induced callbacks. That is, for each potential vulnerability X send an exploit that will ping your server if it fires, then patiently listen.
2016-09-26 12:58:21
source







Gloss