VMware Reports Rise of Deepfake Cybersecurity Attacks — Virtualization Review
News
VMware Reports Rise of Deepfake Cybersecurity Attacks
VMware's eighth annual Global Incident Response Threat Report warns of a rise in the use of deepfakes in cybersecurity attacks, which are increasingly geopolitical in nature and being used more for extortion purposes.
Deepfakes refer to the ability to harness machine learning and artificial intelligence in order to perform actions like replacing a person in a photo or video.
For the purpose of this report, the glossary says a deepfake is synthetic media (audio or video) that is either wholly created or altered by AI or machine learning to convincingly misrepresent someone as doing or saying something that was not actually done or said.
"Cybercriminals are now incorporating deepfakes into their attack methods to evade security controls," said Rick McElroy, principal cybersecurity strategist at VMware, in an Aug. 8 news release announcing the new Global Incident Response Threat Report. "Two out of three respondents in our report saw malicious deepfakes used as part of an attack, a 13 percent increase from last year, with email as the top delivery method. Cybercriminals have evolved beyond using synthetic video and audio simply for influence operations or disinformation campaigns. Their new goal is to use deepfake technology to compromise organizations and gain access to their environment."
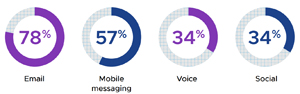
Email was the top delivery method for such attacks (reported by 78 percent of respondents), which VMware said corresponds with the rise in business email compromises (BECs), that is, when criminals send messages that appear to come from a known source with a legitimate request. "From 2016 to 2021, BEC incidents cost organizations an estimated $43.3 billion, according to the FBI," the report said. In fact, it said the FBI recently cited an increase in complaints involving "the use of deepfakes and stolen Personally Identifiable Information (PII) to apply for a variety of remote work and work-at-home positions."
After email, other top delivery methods of deepfake attacks include mobile messaging, voice and social media.
"New platforms are also increasingly being leveraged for such attacks, including third-party meeting applications (31 percent) and business collaboration tools (27 percent), in the form of business communication compromises (BCCs)," the report said. "Scams were cited as these attacks' primary purpose (60 percent), while IT (47 percent) was listed as the top target sector, followed by finance (22 percent) and telecom (13 percent)."
More respondents (58 percent) said deepfake attacks most often took the form of video rather than audio, reported by 42 percent.
Other key findings of the report as presented by VMware include:
- Cyber pro burnout remains a critical issue. Forty-seven percent of incident responders said they experienced burnout or extreme stress in the past 12 months, down slightly from 51 percent last year. Of this group, 69 percent (versus 65 percent in 2021) of respondents have considered leaving their job as a result. Organizations are working to combat this, however, with more than two-thirds of respondents stating their workplaces have implemented wellness programs to address burnout.

[Click on image for larger view.] Burnout Mitigation Programs (source: VMware). - Ransomware actors incorporate cyber extortion strategies. The predominance of ransomware attacks, often buttressed by e-crime groups' collaborations on the dark web, has yet to let up. Fifty-seven percent of respondents have encountered such attacks in the past 12 months, and two-thirds (66 percent) have encountered affiliate programs and/or partnerships between ransomware groups as prominent cyber cartels continue to extort organizations through double extortion techniques, data auctions, and blackmail.
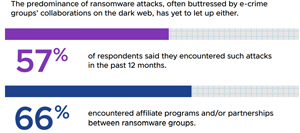
[Click on image for larger view.] Ransomware Doesn't Let Up (source: VMware). - APIs are the new endpoint, representing the next frontier for attackers. As workloads and applications proliferate, 23 percent of attacks now compromise API security. The top types of API attacks include data exposure (encountered by 42 percent of respondents in the past year), SQL and API injection attacks (37 percent and 34 percent, respectively), and distributed Denial-of-Service attacks (33 percent).
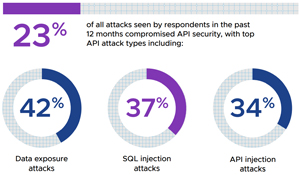
[Click on image for larger view.] Top API Attack Types (source: VMware). - Lateral movement is the new battleground. Lateral movement was seen in 25 percent of all attacks, with cybercriminals leveraging everything from script hosts (49 percent) and file storage (46 percent) to PowerShell (45 percent), business communications platforms (41 percent), and .NET (39 percent) to rummage around inside networks. An analysis of the telemetry within VMware Contexa, a full-fidelity threat intelligence cloud that's built into VMware security products, discovered that in April and May of 2022 alone, nearly half of intrusions contained a lateral movement event.
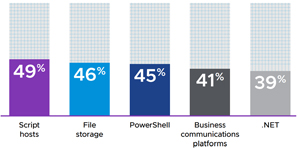
[Click on image for larger view.] Used for Lateral Attack Leverage (source: VMware).
The report also includes some good news: "Defenders are successfully implementing new strategies and methods to stem the tide of incursions. For instance, 75 percent of organizations have employed virtual patching as an emergency mechanism, reflecting the growing maturity of security teams. Nearly 90 percent of respondents now say they are able to disrupt an adversary's activities, and 74 percent report that IR engagements are resolved in a day or less. And while burnout remains a critical issue and a higher number of respondents said they have contemplated leaving their jobs this year than last, overall burnout rates are slightly down from 2021 as organizations take smart steps to address employee wellness."
The report is based on an online survey about trends in the incident response landscape in June 2022, polling 125 cybersecurity and incident response professionals from around the world.








Gloss