March 11th, 2024 | 🕒
https://www.ispeech.org Mar 11, 2024The Hacker NewsCybersecurity / Browser Security As the shift of IT infrastructure to cloud-based solutions celebrates its
June 16th, 2023 | 🕒
iSpeech As Threat Actors Continuously Adapt their TTPs in Today's Threat Landscape, So Must You Earlier this year, threat researchers
February 27th, 2023 | 🕒
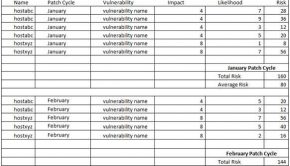
Text to Speech It’s difficult to track ownership of risk issues and measure progress or modifications to the environment. Combine
February 26th, 2023 | 🕒
iSpeech PCI DSS v4.0 permits two approaches for implementing and validating PCI DSS requirements: the traditional method and a customized
February 26th, 2023 | 🕒
iSpeech.org Third-party risk management (TPRM) is a newer term that describes vendor risk management. The Optiv approach focuses on protecting
February 26th, 2023 | 🕒
iSpeech With the latest Verizon Data Breach Incident Report finding that 81 percent of hacking related breaches leveraged either stolen
February 22nd, 2023 | 🕒
iSpeech Organizations face a daily barrage of new vulnerabilities identified in a host of applications and operating systems. Through the
February 21st, 2023 | 🕒
https://www.ispeech.org submitted by /u/Glomar-Response comments] Source link
February 21st, 2023 | 🕒
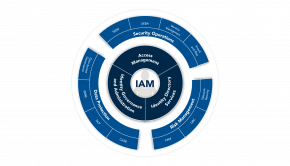
iSpeech In my recent blog post, I discussed the evolution of identity and access management (IAM) and how you should
February 18th, 2023 | 🕒
iSpeech.org Coalfire helps organizations comply with global financial, government, industry and healthcare mandates while helping build the IT infrastructure and
February 11th, 2023 | 🕒
iSpeech.org Getting ready to implement Zero Trust (ZT) isn’t quite as simple as some vendors would have you believe. If
February 4th, 2023 | 🕒
iSpeech.orgUnion Budget 2023-24 takes AI-forward approach to technology and fintech development Firstpost Source link
February 3rd, 2023 | 🕒
Powered by iSpeechEmerging Technologies: Unleashing Their Potential Through a Full-Systems Approach Nasdaq Source link
January 28th, 2023 | 🕒
iSpeech.org Building a whole-of-state approach to cybersecurity | Security Magazine This website requires certain cookies to work and uses other


















Gloss