Leveraging the NIST Cybersecurity Framework For Business
The NIST cybersecurity framework is a powerful tool to organize and improve your cybersecurity program. Today many businesses see cybersecurity with a kind of laissez-faire attitude where they purchase few tools and assign some people to look after their overall IT department. The cybersecurity funding request has got a pushback due to the SMB’s limited resources. Around 32% of SMB security teams find budget their biggest hurdle on the path of following strict cybersecurity measures.
However, many times large cybersecurity budgets get failed to protect the organization from these growing cyberattacks. Thus, the budget doesn’t set security boundaries, it’s all about the strategies. For this, you need a strong security framework to address the particular risks in your budget with no single compromises.
That’s what NIST Cybersecurity Framework is all about that shields your organization from all possible threats. So, continue reading this blog and understand the NIST Cybersecurity Framework and its benefits.
Know the Five Pillars of the NIST Cybersecurity Framework
The NIST cybersecurity framework is based on the five principles that help companies balance risk and security coverage. With this framework, you can help businesses set the proper cybersecurity budget and help determine the possible risk level.
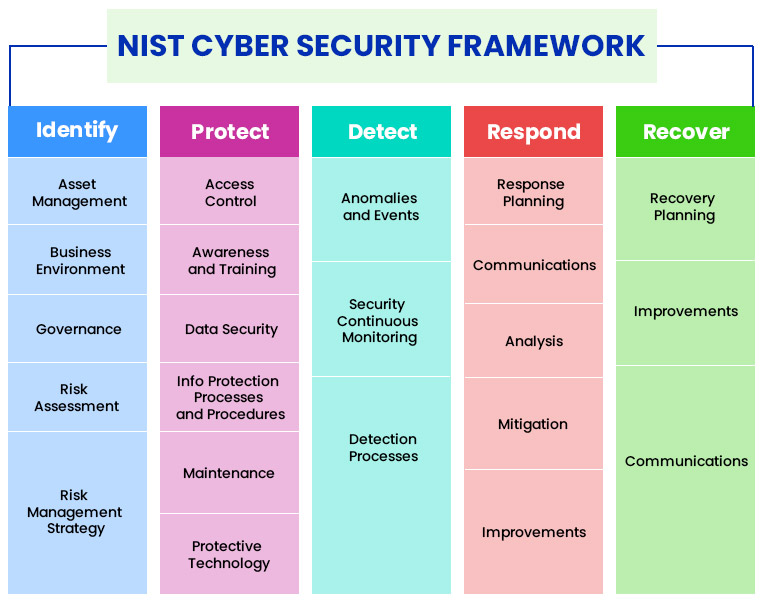
The five pillars of NIST are as follows:
- Identify: Utilize tools to remember every IT asset running in your development and its related cybersecurity vulnerabilities.
- Protect: Take necessary security steps, like protecting logins with multi-factor authentication and training staff to prevent phishing attempts.
- Detect: Setting up the monitoring solutions such as SIEM and IDS and tie them to your organization’s network and a firewall.
- Respond: Implement automation that flags incidents worthy of human attention and directs ticket assignments accordingly.
- Recover: Comprehend how long it takes your organization to recover normal functionality after a cyber-attack or malware event—then understand how long it should take depending on your SLAs.
With these pillars, you can structure your organization’s security strategy and help you identify vulnerable areas. You will certainly form an effective, if not waterproof, defensive cybersecurity business strategy.
Top Benefits of the NIST Cybersecurity Framework
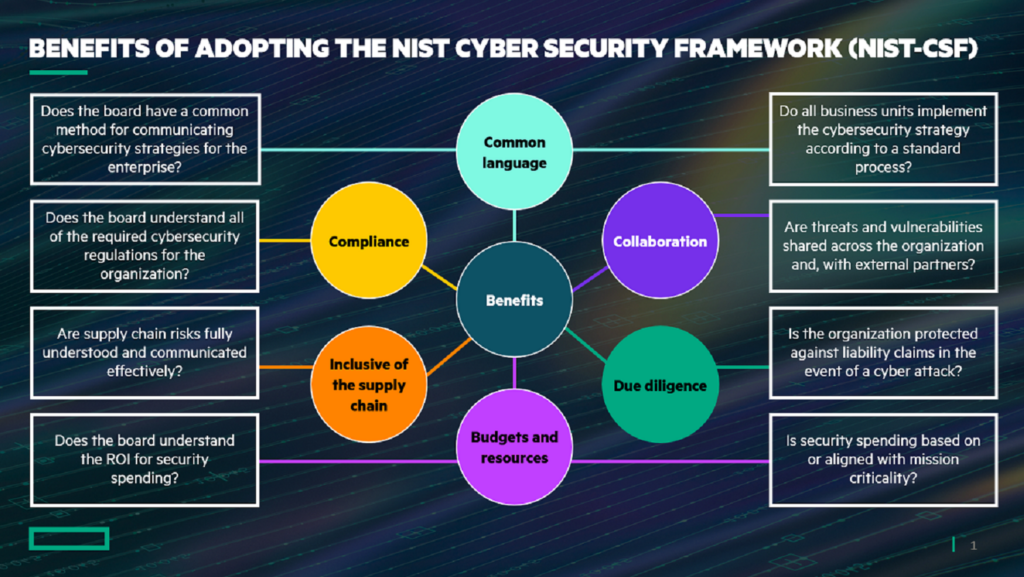
Source: Hewlett Packard Enterprise
The NIST Cybersecurity Framework – also called the Cybersecurity Framework or simply CSF – is a set of standards many companies, governments, and industries have adopted to improve their cybersecurity protocols. The CSF contains many useful features and best practices, but here are some of its core benefits and seven reasons why you should consider using it in your cybersecurity efforts.
1) Helps Organizations Understand Their Risks
The National Institute for Standards and Technology (NIST) developed a cybersecurity framework to help organizations identify risks. The framework also helps an organization understand what needs to be done to manage these risks.
- Assesses vulnerabilities, which are weaknesses that may cause loss or harm to the information system and users.
- Guides reducing vulnerabilities by identifying protective measures that can be put in place or strengthened.
- The framework identifies mitigating factors that will reduce risk after a successful cyber-attack.
- Recommends responses that should be taken if cyber threats are detected.
- Finally, the framework discusses steps to be taken when preparing for recovery from a cyber incident.
The Cybersecurity Framework helps organizations understand how they should take action depending on where they fall in three different tiers: high, medium, and low.
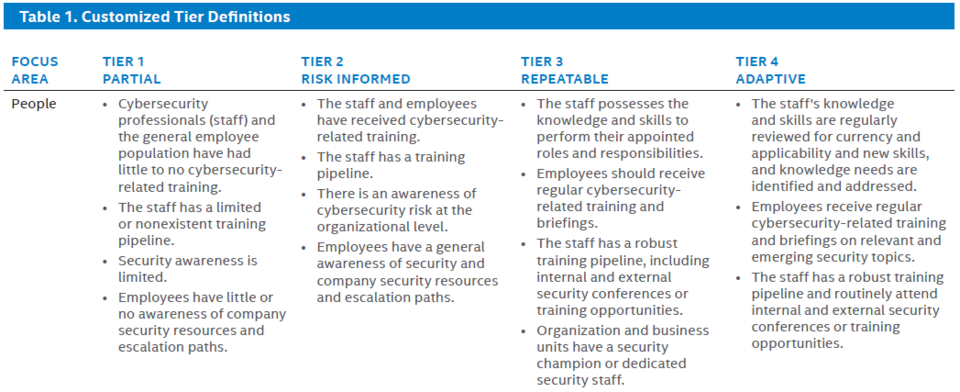
Source: NIST
For example, tier one is a very high risk while tier three is low-risk; tier two falls somewhere between those two levels of risk. When assessing their level of risk, organizations need to consider the likelihood of a security event and its potential severity. If there’s a higher likelihood but less severe consequence, then tier one might be more appropriate. On the other hand, if there’s a lower probability but potentially more severe consequences, tier three might make sense.
2) Facilitates Communication between Stakeholders
NIST cybersecurity framework is a structure that facilitates communication between stakeholders. By understanding your needs and how they fit in with other stakeholders, you can better understand how to protect yourself from attacks best. The framework defines five key functions: Identity, Protect, Detect, Respond, and Recover. Each function has its own set of standards and guidelines to follow.
Federally regulated industries, such as banks, utilities, healthcare providers, etc., are required by law (FERPA) to have an annual assessment for compliance with HIPAA regulations, including an inventory of security risks and controls.
3)Improves an Organization’s Cybersecurity Posture
There are a set of standards to help organizations improve their cybersecurity posture. The framework is designed to be flexible and scalable to be implemented as part of an organization’s existing IT infrastructure. The framework consists of three parts: a core containing essential security functions, practices that guide executing those functions, and five reference models, which offer architectural frameworks for implementing the practices. Organizations can avoid many common cyber-attacks by following the framework methods.
For example, one practice covers managing access control over sensitive data. Without this practice, many critical pieces of information could be vulnerable to attack if hackers access the system with insufficient restrictions or privileges.
By contrast, following this practice protects against unauthorized access by preventing sensitive data from being transferred outside the network without proper authentication credentials or encrypting it when it leaves its source computer (e.g., through email).
4) Encourages the Use of Proven and Tested Solutions
The framework encourages the Use of Proven and Tested Solutions developed through a collaborative process. It also includes a set of standards, guidelines, and practices to improve cybersecurity by providing decision support for organizations that need to make choices about managing their cybersecurity risk. It helps those not security professionals—such as board members, CEOs, and human resource professionals—understand what they should ask from those responsible for information security. It also guides on developing an effective incident response plan, which is critical in reducing harm from cyberattacks.
5) Scalable and Flexible
The framework is scalable and flexible, meaning it can be applied to any organization in any industry. It can also be customized to fit your needs because it does not require rigid adherence to a single methodology.
In addition, the framework is adaptable, meaning that changes in technology or threats will not render it obsolete. It also enables organizations to leverage their security standards and policies to save time creating new ones from scratch. Lastly, the Framework’s use of a common language makes it easier for organizations worldwide to understand what each other is doing for cybersecurity.
Learn the Basics of Cyber Security & Take the Lead: Download eBook
6) Improves an Organization’s Incident Response Capabilities
The National Institute of Standards and Technology (NIST) has published a cybersecurity framework to help organizations improve their incident response capabilities. Organizations can use this framework to guide their approaches to security incident management and help them prepare for cybersecurity emergencies.
For example, Incident Handling Procedures might include
- Performing an assessment.
- Assessing risk.
- Developing containment and recovery procedures.
- Formulating remediation strategies.
A Framework Implementation Plan might include:
- Assigning roles and responsibilities.
- Managing changes in policies, processes, or procedures.
- Developing metrics to measure progress.
In this way, it improves the organization’s overall incident response capabilities and provides a strong security layer to their infrastructure.
7) The Framework Facilitates Regulatory Compliance
The National Institute of Standards and Technology (NIST) Cybersecurity Framework helps organizations identify potential cybersecurity risks. It includes a set of standards, practices, and guidelines to help reduce risk. The framework is flexible and can be used by any organization to secure its data better. The framework also guides organizations on how to use cyber-incident response teams or CIRTs. These groups know what to do if there is an attack on their computer system. A CIRT will help contain the damage from an attack and work with law enforcement when necessary. In addition, it creates a common language for information security professionals so they can better communicate across industries.
Conclusion
The NIST Cybersecurity framework is an excellent way to ensure your company stays up-to-date with cybersecurity standards and practices. You must educate yourself on the framework’s benefits to stay ahead in today’s fast-paced world. No solution can provide complete protection; new vulnerabilities are constantly being discovered as technology advances.
Even without the latest discoveries, we have many more machines, gadgets, and data than we did just a few years ago. Security measures must be continually updated because there will always be more risks than resources available to defend against them.
Recommended Reading:
How To Stay Safe Online – Tips for Getting Cybersmart
CERT-In Certification: What You Need to Know
Why is Cybersecurity Essential for Small Businesses?
The post Leveraging the NIST Cybersecurity Framework For Business appeared first on WeSecureApp :: Simplifying Enterprise Security!.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security! authored by Mahima Jaiswal. Read the original post at: https://wesecureapp.com/blog/leveraging-the-nist-cybersecurity-framework-for-business/







Gloss