Hackers running Linux Operation Windigo are changing tactics targeting porn sites
iSpeech
Security Experts at ESET firm discovered that Windigo campaign is still active and that bad actors are changing their tactics to remain under the radar.
Windigo is a sophisticated malware-based campaign uncovered by security Experts at ESET in March 2014, hackers behind the campaign that exploited the Linux/Ebury backdoor compromising more than 500,000 computers and 25,000 dedicated servers. The Operation Windigo hit popular entities, like the Linux Foundation and cPanel, the hackers compromised a wide range of operating systems, including Apple OS X, FreeBSD, OpenBSD, Microsoft Windows (through Cygwin) and Linux, including Linux on the ARM architecture.
[adsense size='1']
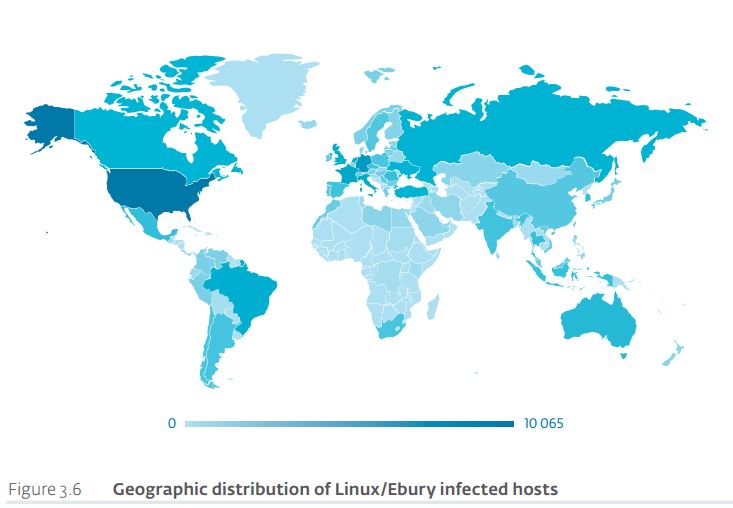
The campaign affected numerous countries including US, Germany, France, Italy, Great Britain, Netherlands, Russian Federation, Ukraine, Mexico and Canada.
Despite the number of infections is smaller than other campaigns, the Windigo operation could be considered high damaging given its compromise of servers and the level of sophistication of the malware.condidered high damaging given its compromise of servers and the level of sophistication of the malware.
ESET malware analyst Olivier Bilodeau has recently explained that bad actors behind Windigo are changing tactic infected porn websites after Windigo was detected by the security community.
[adsense size='1']
The attackers decided to hit content offering adult content because their wide audience, by compromising a single server that can affect thousands of users.
“They were infecting anything with a good IP, but now they are infecting mostly porn sites,” “It’s really stealthy because you are expecting to see pop-ups and banners and who reports issues to porn site? Who reports an exe download attempt? Noone.” “Usually when they infect one server it affects thousands of users.” said Bilodeau.
The operators of Windigo campaign were able to distinguish users from administrators by analyzing for common admin activity, chosen vitims were then redirected to malicious sites serving exploit kits or to dating sites for revenue generation.
The experts at ESET noticed that the attackers behind the Windigo operation used different exploits kits, from Flashback to the BlackHole kit. The infrastructures compromised by Windigo were used to steal SSH credentials, hijack Internet users to malicious websites and send spam.
The attackers behind the Operation Windigo don’t exploit zero-day against Linux or Unix systems, they exploit known weaknesses to build and recruit new machines for their botnets
It is very interesting to note that attackers are targeting smaller “specialised” porn sites, instead great architectures, because they usually have fewer security defenses in place. The tactic allows the bad actors to remain under the radar while they continue to monetize their efforts.
“We think they are interested in staying under the radar and making money, and not spreading too largely [because] law enforcement may be interested if there is a lot of victims,” Bilodeau told to The Register.
[adsense size='1']
Resuming, while ESET firm is discovering much more about the Windigo campaign, the malware author are trying to change tactics to deceive security experts, they are in fact trying to improve their malicious code in order to evade detection mechanisms.
The experts believe that crocks were now engaged in DevOps, malware coders used Bash and Perl scripts streamed through SSH rather than having them physically downloaded to a server. With this ploy, the code was never written on the targeted server, making difficult the investigation of ESET.
“It is the first time we have seen these specific techniques used,” he said.
The only way experts have to analyze the scripts is run <man-in-the-middle on SSH protocol running on a Windigo-infected honeypot. ESET researchers that analyzed the script discovered that that the attacker behind the Windigo campaign targeted specific Linux installations.
“Further statistical analysis was hindered by the absence of command and control servers and the changing nature of the threat meaning extrapolation into the number of victims was “more art than science”.” states The Register.








Gloss