January 31st, 2020 | 🕒
iSpeech How to Hack WPA2 Networks with the PMKID Hashcat Attack Full Tutorial: https://nulb.app/z4ekt Subscribe to Null Byte: https://vimeo.com/channels/nullbyte Subscribe
January 31st, 2020 | 🕒
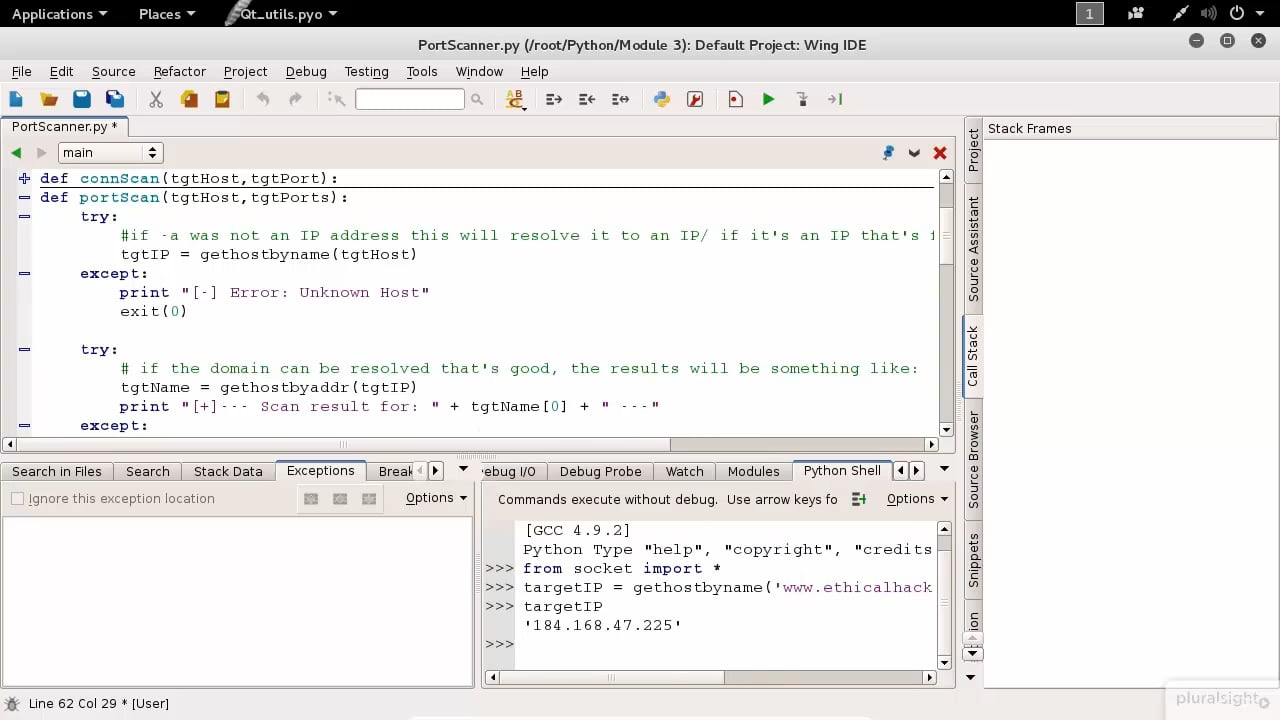
TTS Course: Complete Ethical Hacking & Penetration Testing: Chapter 1 | Network Penetration Testing and Kali Linux Likes: 0 Viewed:
January 31st, 2020 | 🕒
https://www.ispeech.org Course: Complete Ethical Hacking & Penetration Testing: Chapter 1 | Network Penetration Testing and Kali Linux Likes: 0 Viewed:
January 31st, 2020 | 🕒
Text to Speech É por isso que chamam o Kali Linux de "Sistema dos Hackers". Entre no nosso Canal no
January 31st, 2020 | 🕒
https://www.ispeech.org Course: Complete Ethical Hacking & Penetration Testing: Chapter 1 | Network Penetration Testing and Kali Linux Likes: 0 Viewed:
January 31st, 2020 | 🕒
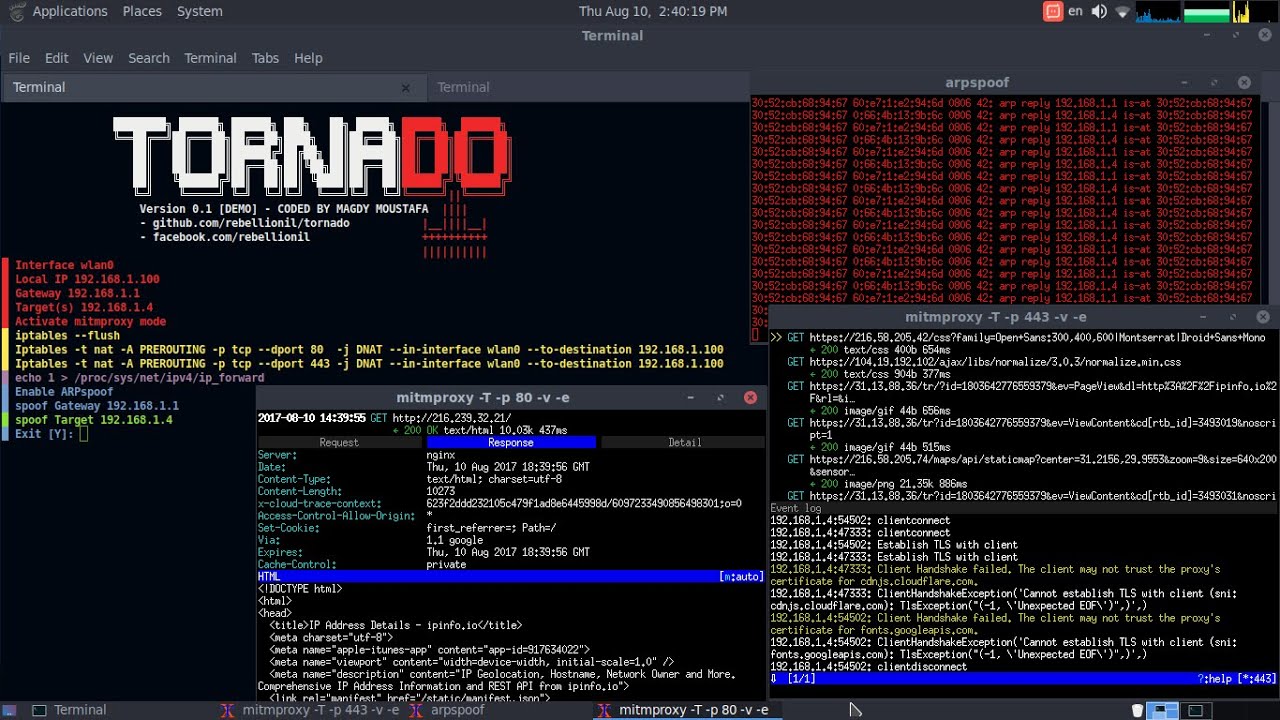
https://www.ispeech.org git clone https://github.com/rebellionil/tornado cd tornado bash setup.sh https://github.com/reb311ion/tornado Version release: 0.2-STABLE Author: Magdy ... source
January 31st, 2020 | 🕒
Convert Text to Speech Florida police said they arrested two suspects after a black SUV managed to breach two security
January 31st, 2020 | 🕒
TTS Demo And it only took, er, four and a half months for people to see sense Dramatization – may
January 31st, 2020 | 🕒
iSpeech.org How to download and install the latest and greatest Kali Linux 2020.1 (no default root access) source
January 31st, 2020 | 🕒
Text to Speech The OWASP Risk Assessment Framework consist of Static application security testing and Risk Assessment tools, Eventhough there
January 31st, 2020 | 🕒
https://www.ispeech.org Joey Sasso | Vs The Internet View at DailyMotion


















Gloss