April 28th, 2014 | 🕒
iSpeech Setting up a trapdoor one-way function Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/rsa-encryption-step-3?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/intro-to-rsa-encryption?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Computer Science on
April 28th, 2014 | 🕒
iSpeech Measuring the divisibility of a number Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/rsa-encryption-part-4?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/rsa-encryption-step-3?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Computer Science on
April 28th, 2014 | 🕒
Text to Speech Introduction to why we would need RSA Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/rsa-encryption-step-2?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/diffie-hellman-key-exchange-part-2?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience
April 28th, 2014 | 🕒
iSpeech.org Walkthrough of Diffie-Hellman Key Exchange Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/intro-to-rsa-encryption?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/discrete-logarithm-problem?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Computer Science on Khan
April 28th, 2014 | 🕒
iSpeech.org A mathematical lock using modular arithmetic Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/diffie-hellman-key-exchange-part-2?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/diffie-hellman-key-exchange-part-1?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Computer Science on
April 28th, 2014 | 🕒
iSpeech Why do we need public key cryptography? Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/discrete-logarithm-problem?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.khanacademy.org/computing/computer-science/cryptography/modern-crypt/v/the-fundamental-theorem-of-arithmetic-1?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Computer Science
April 28th, 2014 | 🕒
iSpeech WW2 Encryption is explored with a focus on the Enigma. Read more here. Watch the next lesson: https://www.khanacademy.org/computing/computer-science/cryptography/crypt/v/perfect-secrecy?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed
April 28th, 2014 | 🕒
text to speech Claude Shannon's idea of perfect secrecy: no amount of computational power can help improve your ability to
April 28th, 2014 | 🕒
iSpeechThe BlindElephant Web Application Fingerprinter attempts to discover the version of a (known) web application by comparing static files at
April 28th, 2014 | 🕒
iSpeech Victims project for securing your Java project Victims project for securing your Java project Monday, Apr 28, 2014, 12:00
April 28th, 2014 | 🕒
Convert Text to Speech We've got a look back at the Mr. LO competition, the IRC has new laptops for
April 28th, 2014 | 🕒
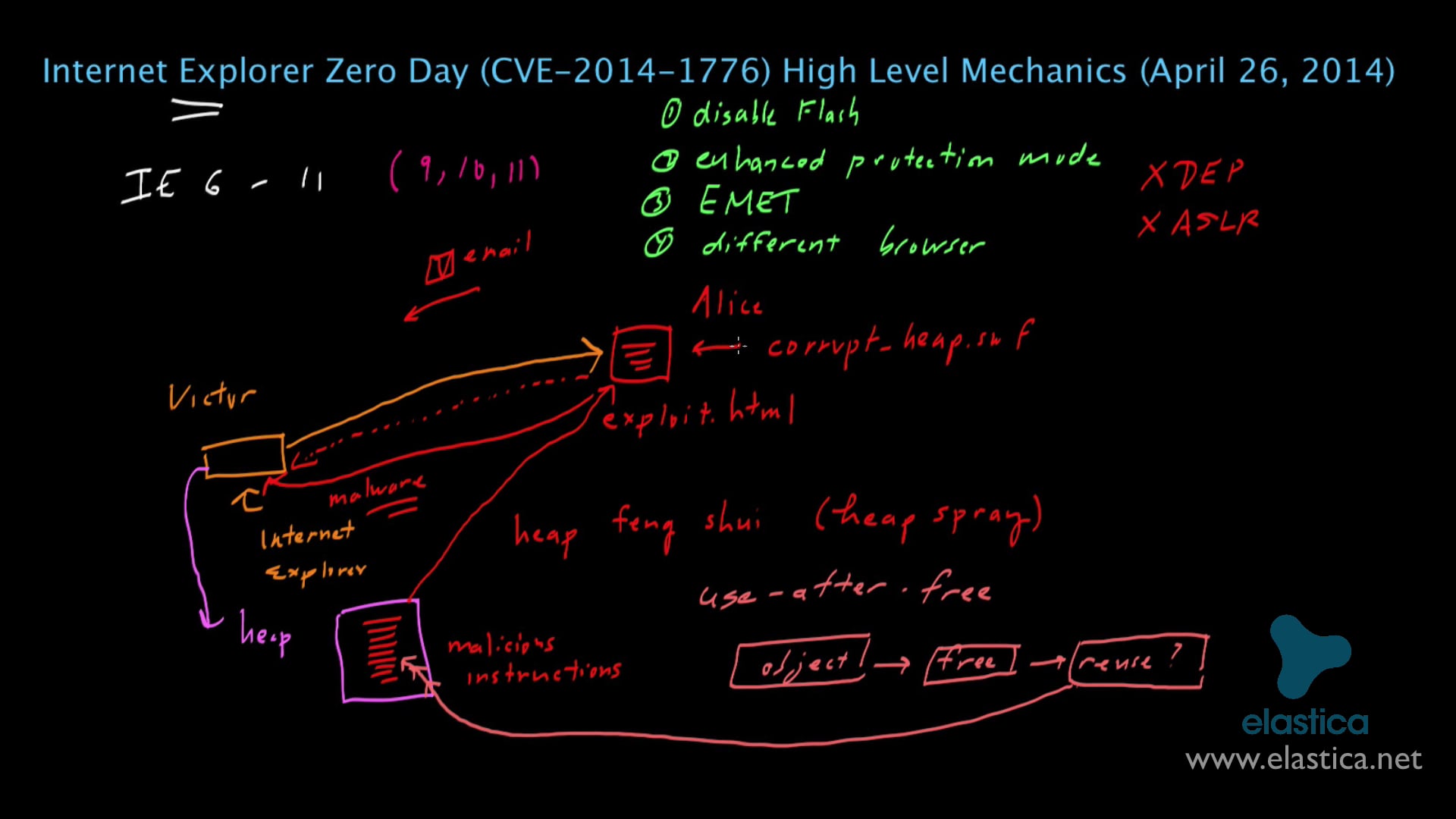
https://www.ispeech.org/text.to.speech On April 26, 2014, a new Internet Explorer Zero Day Vulnerability (CVE-2014-1776) was discovered. The exploit involves taking advantage
April 28th, 2014 | 🕒
Text to Speech Voices Get Full Course: http://www.engineeringmentor.com/CNYTv3 Networks #3: This tutorial introduces the Cryptography basics. It also explains what
April 28th, 2014 | 🕒
Powered by iSpeech http://www.techgig.com/expert-speak/SQL-Injections-529 One of the most notorious technique trouble almost all the application over the internet is SQL




















Gloss